www.magazine-industry-usa.com
12
'10
Written on Modified on
Trustable Wireless solution, based on 802.11 standards
While the number of adopters of industrial wireless is fast increasing worldwide, some Automation Engineers are still sceptical regarding security. This is an important topic. And no one will consider these questionings illegitimate. This article will bring answers and hopefully help convince them that security should not be the reason for postponing the pace they will do towards wireless.
One option is to use a FHSS (Frequency Hopping Spread Spectrum) solution. The radios are using a proprietary wireless protocol and no radio can enter the dance from outside of the network. But most of the users want to go with standard solutions, based on the IEEE 802.11 series (commonly referred to as “Wi-Fi” solutions).
Security!
The primary means of security in radios based on the IEEE standards is adherence to the IEEE 802.11i standard for secure wireless communications. In addition, ProSoft Technology’s RadioLinx solutions support several other mechanisms to enhance the security offering.
The primary means of security in radios based on the IEEE standards is adherence to the IEEE 802.11i standard for secure wireless communications. In addition, ProSoft Technology’s RadioLinx solutions support several other mechanisms to enhance the security offering.
IEEE 802.11i
In 2004, the IEEE published the IEEE 802.11i standard to resolve security concerns regarding 802.11 communications. This standard is often referred to as WPA2, a term originated by the Wi-Fi Alliance.
The fundamental improvement made to 802.11 security by the adoption of the 802.11i standard is the use of the AES block cipher as the encryption engine. The use of AES addressed many of the weaknesses of the previous 802.11 encryption techniques including weaknesses in the key scheduling algorithm.
Several other significant improvements were also incorporated into 802.11i to resolve security issues including authentication issues, replay attacks and data forgery.
In 2004, the IEEE published the IEEE 802.11i standard to resolve security concerns regarding 802.11 communications. This standard is often referred to as WPA2, a term originated by the Wi-Fi Alliance.
The fundamental improvement made to 802.11 security by the adoption of the 802.11i standard is the use of the AES block cipher as the encryption engine. The use of AES addressed many of the weaknesses of the previous 802.11 encryption techniques including weaknesses in the key scheduling algorithm.
Several other significant improvements were also incorporated into 802.11i to resolve security issues including authentication issues, replay attacks and data forgery.
AES Encryption
The AES encryption algorithm with a 128-bit key was approved by the US government in 2003 for use in encrypting classified information. In addition, AES was approved by the NSA for Top Secret information. The RadioLinx radios support use of 128-bit AES encryption for all communications, which is the highest level of encryption allowed for export by the US government.
AES is a block cipher which is efficient to implement in hardware so that it does not degrade the speed of communications. The RadioLinx is able to maintain full data throughput while performing 802.11i encryption and decryption on all packets being transferred.
One significant improvement in AES over previous implementations of 802.11 security is that it is not possible to extrapolate the encryption key being used by the radios by observing the encrypted communications.
The AES encryption algorithm with a 128-bit key was approved by the US government in 2003 for use in encrypting classified information. In addition, AES was approved by the NSA for Top Secret information. The RadioLinx radios support use of 128-bit AES encryption for all communications, which is the highest level of encryption allowed for export by the US government.
AES is a block cipher which is efficient to implement in hardware so that it does not degrade the speed of communications. The RadioLinx is able to maintain full data throughput while performing 802.11i encryption and decryption on all packets being transferred.
One significant improvement in AES over previous implementations of 802.11 security is that it is not possible to extrapolate the encryption key being used by the radios by observing the encrypted communications.
Authentication
A second major improvement in the 802.11i security implementation is to prevent problems caused by communication with devices which should not have been allowed on the network. Previous 802.11 security was susceptible to allowing 802.11 client devices to communicate with access points which emulated network access points. When a client would begin to communicate with one of these rogue access points, the rogue access point could extract information from the client device, presenting a major security flaw.
The 802.11i standard has much improved authentication, requiring both the access point and the clients to authenticate that they are allowed in the network before communications begins. The 802.11i term to describe this process is the four-way handshake. In this process, the access point and client exchange packets encrypted with a shared key. Both units must contain identical shared keys in order for the authentication to complete successfully.
Once the authentication has completed, the two units exchange a temporal key that will be used for encrypting communications. The temporal key is refreshed periodically by the two units as an added means of security.
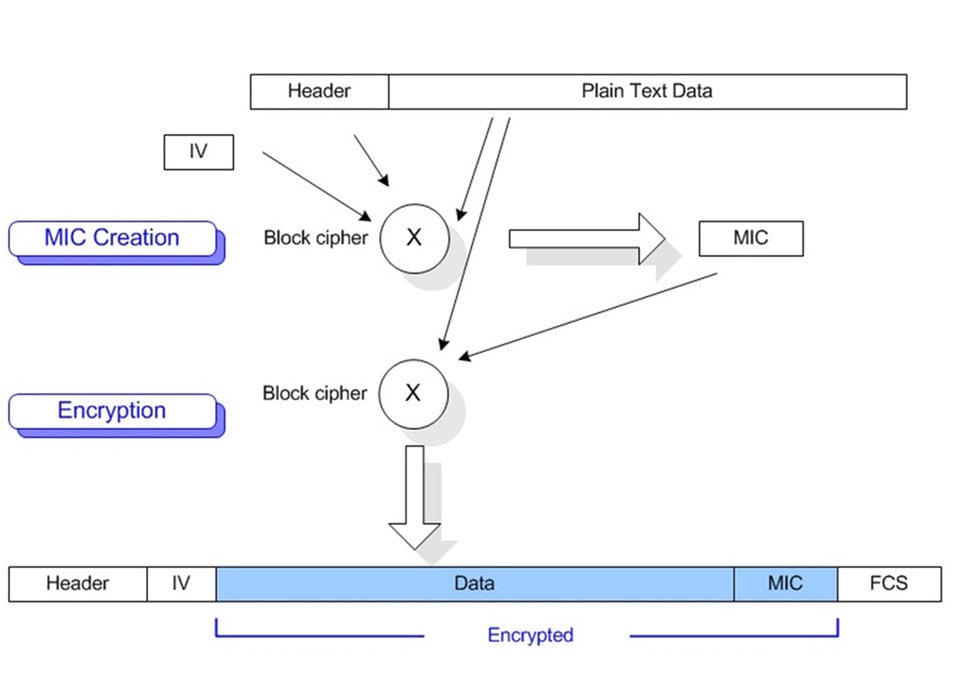
Message Integrity Check
The mechanisms in 802.11i described above prevent unauthorized decryption of messages and prevent the key from being stolen so that messages could be encrypted and decrypted. A third improvement in 802.11i is to prevent fictitious data from being generated by an unauthorized user that could have a negative impact on the system.
The 802.11i standard added an improved message integrity check specifically to prevent replay attacks and forged data. Replay attacks constitute replaying a message over the air that was previously transmitted with the intent of having the receiver pass the data through to the Ethernet network. Forged data attacks constitute making minor changes to the encrypted data stream to generate bad packets on the Ethernet. Previous 802.11 security was susceptible to both of these issues.
The 802.11i mechanism uses a 48-bit initialization vector as well as the MAC ID of the transmitter and receiver in a hashing mechanism to generate an integrity check sequence that is used to validate each message. It avoids replay attacks by blocking identical packets that have been received previously. Once a packet has been successfully received, decrypted and passed to the Ethernet, subsequent identical packets are discarded. It is also successful at avoiding forged data attacks. Additionally, if multiple packets are received from a source that appears to be forging data, a client will disassociate itself and re-associate in order to generate a new secure set of keys.
The mechanisms in 802.11i described above prevent unauthorized decryption of messages and prevent the key from being stolen so that messages could be encrypted and decrypted. A third improvement in 802.11i is to prevent fictitious data from being generated by an unauthorized user that could have a negative impact on the system.
The 802.11i standard added an improved message integrity check specifically to prevent replay attacks and forged data. Replay attacks constitute replaying a message over the air that was previously transmitted with the intent of having the receiver pass the data through to the Ethernet network. Forged data attacks constitute making minor changes to the encrypted data stream to generate bad packets on the Ethernet. Previous 802.11 security was susceptible to both of these issues.
The 802.11i mechanism uses a 48-bit initialization vector as well as the MAC ID of the transmitter and receiver in a hashing mechanism to generate an integrity check sequence that is used to validate each message. It avoids replay attacks by blocking identical packets that have been received previously. Once a packet has been successfully received, decrypted and passed to the Ethernet, subsequent identical packets are discarded. It is also successful at avoiding forged data attacks. Additionally, if multiple packets are received from a source that appears to be forging data, a client will disassociate itself and re-associate in order to generate a new secure set of keys.
Secondary Security Mechanisms
In addition to use of 802.11i security, the RadioLinx solutions support several other mechanisms to enhance the security.
MAC Filtering.The RadioLinx allows the user to enter the MAC IDs of the radios that are allowed to associate to it. When this filter is implemented, only traffic from devices with these MAC IDs will be allowed. Any devices with other MAC IDs will be ignored.
Hidden SSID. The RadioLinx allows the user to remove the SSID from its 802.11 beacon. This makes it more difficult for unauthorized users to detect the name of the network and attempt association.
Block General Probe.The RadioLinx supports a setting that tells the radio that it should not respond to 802.11 probe requests that are not directed for a specific SSID. The typical mechanism for a client to associate with an access point is for it to send a probe request to determine if there are any access points in the area. A general probe request elicits responses from access points of any SSID. By preventing this, the client which desires to associate with the radio must be aware of the SSID ahead of time in order to send a probe request specifically for that SSID.
In addition to use of 802.11i security, the RadioLinx solutions support several other mechanisms to enhance the security.
MAC Filtering.The RadioLinx allows the user to enter the MAC IDs of the radios that are allowed to associate to it. When this filter is implemented, only traffic from devices with these MAC IDs will be allowed. Any devices with other MAC IDs will be ignored.
Hidden SSID. The RadioLinx allows the user to remove the SSID from its 802.11 beacon. This makes it more difficult for unauthorized users to detect the name of the network and attempt association.
Block General Probe.The RadioLinx supports a setting that tells the radio that it should not respond to 802.11 probe requests that are not directed for a specific SSID. The typical mechanism for a client to associate with an access point is for it to send a probe request to determine if there are any access points in the area. A general probe request elicits responses from access points of any SSID. By preventing this, the client which desires to associate with the radio must be aware of the SSID ahead of time in order to send a probe request specifically for that SSID.
Convinced about security!
And what about reliability? How am I sure that my network is reliable and safe enough for transmitting my control data? Well, this could be the object of another article with specific highlight on 802.11n solutions (see the new RadioLinx Industrial 802.11n solutions from ProSoft Technology). This new IEEE standard allows multiple networks to coexist in the same location (22 non-overlapping channels); and due to the way it handles multipath (multiple reflexions) it is offering robust connectivity and allows high speed for data transfers (up to 300 Mbps over the air). Without going too deep in theory, let’s say that industrial 802.11n technology is a good fit for many automation applications. In the meantime, consider that high speed systems such as bottling machines or hoister-cranes have gained in reliability and productivity thanks to… RadioLinx industrial wireless.
And what about reliability? How am I sure that my network is reliable and safe enough for transmitting my control data? Well, this could be the object of another article with specific highlight on 802.11n solutions (see the new RadioLinx Industrial 802.11n solutions from ProSoft Technology). This new IEEE standard allows multiple networks to coexist in the same location (22 non-overlapping channels); and due to the way it handles multipath (multiple reflexions) it is offering robust connectivity and allows high speed for data transfers (up to 300 Mbps over the air). Without going too deep in theory, let’s say that industrial 802.11n technology is a good fit for many automation applications. In the meantime, consider that high speed systems such as bottling machines or hoister-cranes have gained in reliability and productivity thanks to… RadioLinx industrial wireless.

